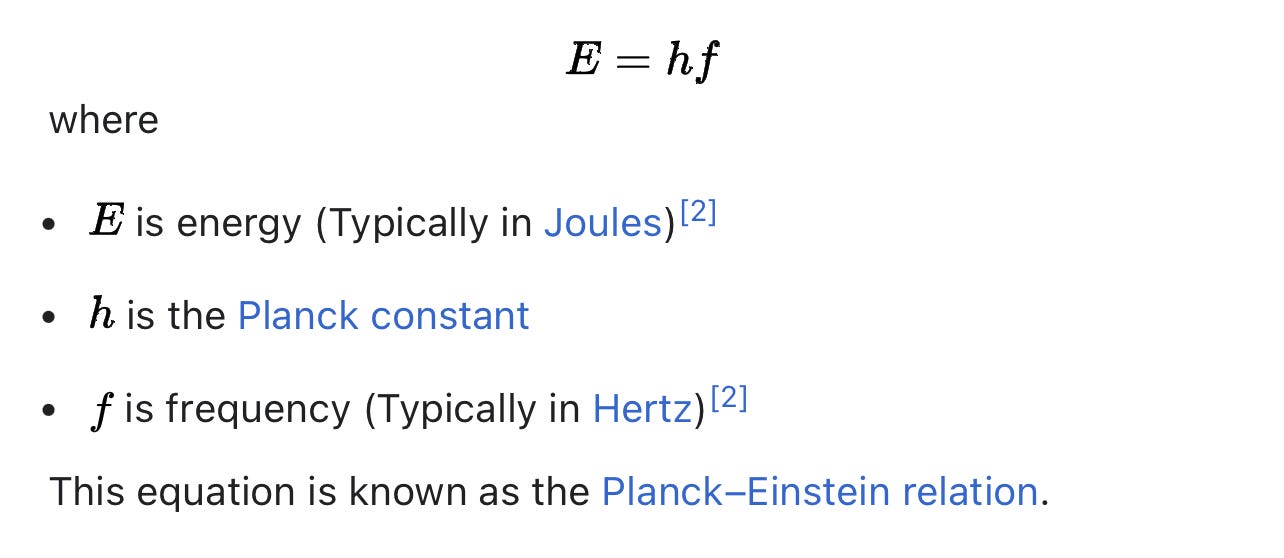Disregard every other messaging app—let’s talk about Signals Amnesia.
Quantum resistance end-to-end encryption will be the most secure method in the near future, but even that won’t suffice forever.
A good ol’ face-to-face conversation is almost the most secure way to communicate; besides dead drops.
But even speaking in person has its vulnerabilities. Someone could be listening with a parabolic ear; your electronic device with a microphone can be bugged and boy the microphone response on these devices are better than you think. Not to forget that radio frequency can be intercepted even off a call. The academic exploit actually works similar to a transducer from a parabolic ear sniffing the frequency even without a battery, altogether it works like Radio-frequency identification (RFID).
Inductive coupling used to transmit the energy to different functional areas in the wearable device drives various integrated circuits. Based on experimental results, this system is a stable and efficient method to transfer energy and signals—IEEE.
The thought that you can send bits over the internet securely is a marketing tactic and counter tactics to catch foreign and domestic terroristic threats—oh you use burners; you’re a “haCk3r”, or a fond user of tor? Anyway, let’s be realistic, you’re trying to fool the same people who designed the technology down to the physics of the photons?
Recommend | Xybercraft ™
Cryptographer literally dream of ciphers and in a world of data it’s all about transmissions.
Is it really all about the zeros and ones?
Advance Encryption Standard (AES-256) is only as strong as the key, right?
For AES-128, the key can be recovered with a computational complexity of 2126.1 using the biclique attack. For biclique attacks on AES-192 and AES-256, the computational complexities of 2189.7and 2254.4 respectively apply. Related-key attacks can break AES-256 and AES-192 with complexities 299.5 and 2176 in both time and data, respectively.
The researchers that discovered the method weren’t even on a government payroll. So if you factor in government power then we’re on a road where there is probably more than likely more than one way to extract or decrypt information, it’s just highly classified and continuously denied.
Signal uses additional measures to counter brute forcing on top of the common security schemes such as:
Argon2—designed by Alex Birtukov, Daniel Dinu, and Dmitry Khovratovich from the Univeristy of Luxembourg. Argon2 is what’s known as a key derivation function cryptographic algorithm with a hash function digest up 232 bytes in length; Argon2 algorithms are based on BLAKE2 and the KDF was originally publicly recognized in 2015 at the Password Hashing Competition. I’ll touch up a bit more on Argon2 and how it’s it used later.
Confusion is control.
So let’s be sycophantic—hash based combinations; privacy and protection based on string values—I guess it’s good that an ordinary neighbor or malicious employee isn’t trying to snoop your business on their free time.
Signal is the closest you will get to the unbreakable Sigaba mechanism.
Recommend | Xybercraft ™
How Signal actually works—storing your information (data)
Signal doesn’t want to be responsible for handling much of your data especially plaintext records of you or your information. This includes your profile photo other information like: social graphs, locations, or groups attributes; data is stored temporarily in their cloud, and wants to avoid fingers being pointed at them as much as possible, this is why if you have ever deleted the app and logged back in everything was gone unless you transferred it, and if you have transferred—what you transfer is encrypted in transmission and was/is actually stored on your device and not their servers, beautiful right? This is the beauty of Open Source. You can see what technology is in use, and how it is used—unlike other big names that hide everything to “reduce vulnerabilities.”
At Signal, we want to make privacy simple. From the beginning, we’ve designed Signal so that your information is in your hands rather than ours—Signal.org
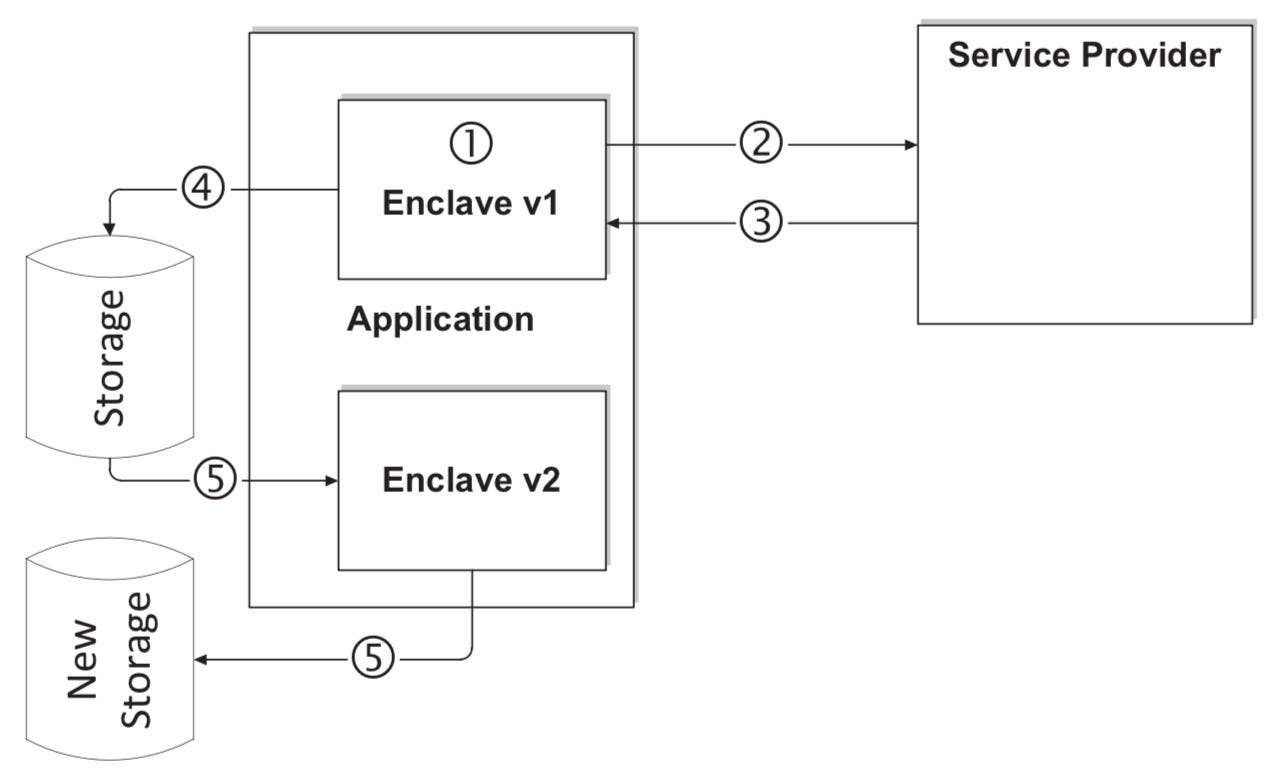
Signal uses a genius design with Intel® Software Guard Extensions (Intel® SGX) technology to create Enclaves.
This advanced feature was published almost 10 years ago and it allows a hardware entity or a combination of hardware and software to gain a remote provider's (also known as the relying party) or producer's trust through a container process to prevent attacks while safeguarding data. It works with access control policies over the air or wire provisioning enclave(s) that encrypts the data for later use with the following steps.
1: Enclave Launch » 2: Attestation » 3: Provisioning » 4: Sealing/Unsealing » 5: Software Upgrade
Finally, when platform owners plan to transfer ownership of the platform, the secrets available during their ownership period should be made inaccessible.
Intel® SGX includes a user owned special persistent value that, when changed, changes all keys available to software.
Signal also doesn’t want to store you data and fully encrypt it with a key you can save and use to access it whenever you want because ish happen and if you lose the key then you will be locked out of your data until publicly known exploits are readily available to decrypt your information. This is why originally companies store your information in their servers in plaintext to be able to retrieve the data.
How is Signal private if they use my phone number?
I’m glad you asked because I thought the same thing signing up myself lol. So you know how you create a password (passphrase, passkey) whenever you get going on the enrollment process?
Memorable passwords used with password-based encryption are often so weak that they are easy to brute force. Randomly generated pass phrases strong enough to resist brute forcing are often too long to be memorable.
So, warning we will be speaking in cryptography lingo if you’re ready let’s dive in.
Recommend | Xybercraft ™