Yubico's FIDO 140-3 Compliant HSM Set to Launch by Mid to Late 2025?
As FIPS 140-2 certifications approach their sunset in 2026, transitioning to modern, validated HSM solutions ensures ongoing compliance and security like Yubikey 6:
What is FIPS 140-3?
FIPS 140-3, which stands for Federal Information Processing Standard 140-3, is a security standard developed by the U.S. and Canadian governments to validate cryptographic modules used in protecting sensitive information. It is an updated version of the earlier FIPS 140-2 standard and was officially released in 2019 to address evolving security challenges and align with the international standard ISO/IEC 19790. The purpose of FIPS 140-3 is to ensure that cryptographic modules—such as hardware, software, or firmware components—meet rigorous security requirements for safeguarding data against unauthorized access or tampering.
The standard defines four distinct levels of security, each tailored to different operational environments and risk profiles. Level 1 focuses on basic cryptographic functionality and requires minimal physical security, while Level 4 provides the highest level of protection, including advanced tamper detection, environmental resistance, and multi-factor authentication. This tiered approach allows organizations to select a level that matches their specific needs, whether they are securing consumer devices or highly sensitive government systems. One of the key features of FIPS 140-3 is its emphasis on lifecycle testing and validation. Cryptographic modules must undergo extensive testing to ensure they operate securely under various conditions and remain resilient against physical and logical attacks. The standard also includes requirements for mitigating environmental risks such as temperature fluctuations or electromagnetic interference, ensuring that cryptographic systems remain reliable even in harsh environments.
Compliance with FIPS 140-3 is mandatory for U.S. federal agencies and contractors handling Sensitive But Unclassified (SBU) data, as well as for organizations in regulated industries such as healthcare, finance, and defense. Failure to comply can result in penalties or loss of contracts, making adherence to this standard critical for entities working with government systems or sensitive information. FIPS 140-3 plays a crucial role in modern cybersecurity by providing a trusted framework for developing and validating cryptographic solutions that protect data integrity and confidentiality. Its adoption extends beyond government use, as private sector organizations also rely on it to ensure their systems meet high-security standards. By addressing emerging threats and incorporating global best practices, FIPS 140-3 helps maintain the integrity of cryptographic systems in an increasingly interconnected and threat-prone digital landscape.
Recommend | Xybercraft ™
The Key Mathematical and Technical Improvements in FIPS 140-3 security compared to FIPS 140-2
Encryption Strength: FIPS 140-3 enforces the use of AES encryption with a minimum key size of 128 bits. This provides 2^128 possible key combinations, which is significantly stronger than older algorithms like SKIPJACK (80-bit) keys 2^80 possibilities.
Digital Signatures: Digital signatures must now meet or exceed a security level of 112 bits, such as those provided by elliptic curve cryptography (e.g., ECDSA). This ensures resistance to brute force attacks up to 2^112 attempts.
Hash Algorithms FIPS 140-3 includes updated guidance for secure hash functions like SHA-3, which provides collision resistance of 2^256 for SHA-256, making it more secure than older hashing methods.
Self-Testing Requirements: Introduces stricter self-testing procedures, such as pre-operational self-tests and conditional algorithm tests, to ensure the integrity of cryptographic modules before they are used.
Why the Transition Matters
FIPS 140-2 certifications will remain valid until September 2026 but will eventually be replaced by FIPS 140-3 requirements. The updated standard reflects advancements in cryptographic technology and better addresses modern security threats, ensuring stronger protection for sensitive data.
What is a Hardware Security Module (HSM)?
A Hardware Security Module (HSM) is a specialized physical device designed to provide a high level of security for cryptographic keys and operations. These devices are engineered to be tamper-resistant, meaning they are built to withstand physical and logical attacks. HSMs are essential components in modern cybersecurity architectures, as they handle critical tasks such as generating, storing, and managing cryptographic keys used for encryption, decryption, digital signatures, and authentication.
Recommend | Xybercraft ™
Key Functions of HSMs
Key Generation: HSMs can generate cryptographic keys in a secure environment, ensuring that the keys are created in a way that minimizes the risk of exposure or compromise.
Key Storage: They provide a secure location for storing sensitive cryptographic keys. This prevents unauthorized access and ensures that keys are only used within the secure confines of the HSM.
Cryptographic Operations: HSMs can perform various cryptographic operations, such as encrypting and decrypting data or generating digital signatures, all while keeping the keys secure and isolated from potential threats.
Compliance and Auditing: Many industries are subject to strict regulatory requirements regarding data protection. HSMs help organizations comply with standards such as FIPS 140-2 (Federal Information Processing Standards) by providing documented security controls and audit trails.
Why Should You Use a HSM?
Enhanced Security: HSMs provide a robust defense against both physical and cyber threats. Their tamper-resistant design helps protect against unauthorized access or manipulation of cryptographic keys.
Data Protection: By securely managing encryption keys, HSMs help safeguard sensitive data from breaches. This is particularly crucial for industries like finance, healthcare, and government, where data integrity and confidentiality are paramount.
Operational Efficiency: HSMs streamline cryptographic processes by centralizing key management and reducing the complexity of handling encryption tasks across multiple systems.
Regulatory Compliance: Many organizations face stringent compliance requirements regarding data security. Implementing an HSM can help demonstrate adherence to these regulations, making it easier to pass audits and avoid penalties.
Scalability: As organizations grow and their data protection needs evolve, HSMs can scale to accommodate increased workloads without compromising security.
Is FIPS 140-3 the best security?
By adopting FIPS 140-3-compliant modules, organizations can benefit from improved cryptographic strength, enhanced physical security measures, and alignment with international standards for secure systems.
FIPS 140-3 (For Non-Classified Information)
Designed to protect sensitive information that is not classified.
Utilizes publicly known cryptographic algorithms such as AES with a minimum of 128-bit keys and RSA with at least 2048-bit keys.
Certification is handled by the National Institute of Standards and Technology (NIST) through the Cryptographic Module Validation Program (CMVP).
NSA Type 1 Encryption (For Classified Information)
Used to secure classified data, including Secret and Top Secret information.
Employs highly secure, classified algorithms and techniques that are not publicly disclosed.
Certification is conducted by the National Security Agency (NSA), with strict rules on handling, storage, and export.
In essence, FIPS 140-3 is intended for environments dealing with non-classified sensitive data, ensuring compliance with modern security standards. In contrast, NSA Type 1 encryption is reserved for classified information, offering the highest level of security.
Related: Can the regular public use a more secure method like the NSA?
What and who is Yubico?
Yubico is a cybersecurity firm based in Sweden, established in 2007 by Stina and Jakob Ehrensvärd. The company is renowned for its innovative hardware authentication solutions, particularly the YubiKey, which is widely used for securing online accounts and systems.
These keys can connect via USB or NFC and offer several key features:
Increased Security: They provide robust protection against phishing and unauthorized access.
Convenient Login: Users can authenticate quickly with a simple touch, eliminating the need for passwords.
Support for Passwordless Access: YubiKeys work with various authentication protocols like FIDO2/U2F and WebAuthn.
What is a YubiKey?
A YubiKey is a compact hardware device designed to enhance security through strong authentication methods. YubiKeys, particularly the YubiKey 5 FIPS Series, supports both FIDO2 and PIV protocols, meeting the highest authenticator assurance level 3 (AAL3) as per NIST SP800-63B guidelines
Recommend | Xybercraft ™
Benefits of Using a YubiKey
There are several compelling reasons to consider using a YubiKey:
Mitigates Attack Risks: Provides strong defense against remote hacking attempts.
Unique and Secure: The keys cannot be easily copied or compromised.
Cost-Effective: Reduces the need for IT support related to password recovery and management.
Wide Compatibility: Works with numerous applications and services.
Faster Logins: Offers quicker access compared to traditional authentication methods.
Research has shown that organizations implementing YubiKeys can significantly lower the risk of credential theft, achieving impressive returns on their investment. Yubico serves a wide range of industries, including retail, healthcare, telecommunications, and technology, with customers located in over 160 countries, its plenty enough for you.
YubiKey offers hardware-based authentication, using phishing-resistant protocols such as FIDO2 and PIV, ensuring compliance with AAL3 as per NIST SP800-63B guidelines.
It employs robust cryptographic algorithms: including AES-256, RSA (2048, 3072, 4096), and ECC (P-256, P-384), providing extensive compatibility across various systems.
Supports HMAC-based and TOTP algorithms: (HOTP and TOTP) for secure authentication.
Functions as an OpenPGP card, enabling secure signing and encryption without exposing private keys.
This interoperability makes YubiKey a versatile solution—for enhancing security across multiple applications.
When can I purchase the new YubiKey?
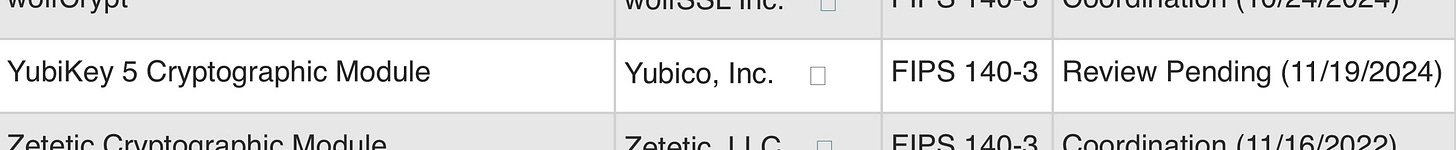
Well don’t hold your breath, the Cryptographic Module Validation Program (CMVP) is backed up running tests on many other submissions, from big name like AMD, Apple, Amazon, Thales, SonicWall, etc., some of them were submitted in 2023. Seeing the newer YubiKey in 2025 would be great but I, nor Jeff promised it was going to see an official release date just yet. Biggest question is—will it actually be launched in 2025 or is that when it will likely be approved? I have a feeling It honestly might not launch until 2026, but only time will tell.
We’re excited to share that the YubiKey 5 FIPS Series latest 5.7.4 firmware has completed testing by our NIST accredited testing lab, and has been submitted to the Cryptographic Module Validation Program (CMVP) for FIPS 140-3 validation, Overall Level 2 and Physical Level 3.
Accommodating up to 100 device-bound passkeys (up from 25), 64 OATH seeds (up from 32), 24 PIV certificates, and 2 OTP seeds at once for a total of 190 credentials.
Including support for larger RSA keys (RSA-3072 and RSA-4096) and Ed25519, key types enhances key management functions and flexibility for organizations, aligning with DoD memo requirements on stronger public key algorithms.
Check out: FIPS 140-3 Article by Jeff Wallace.
Should I wait to by the newer YubiKey?
Probably not, they really aren’t that expensive to help manage your accounts or devices, on top of that what if you lose access to your email or phone number—this has been a safer way to protect yourself for quiet awhile now.
FIPS 140-2, YubiKey 5 Cryptographic Module(s) aren’t nothing to overlook for protection from someone stealing your property or trying to bypass your standard 2FA.
Tested by: Penumbra Security, Inc
The YubiKey 5 FIPS Series is IP68 rated, crush resistant, no batteries required, and no moving parts.
Compatible with major operating systems such as Microsoft Windows, macOS, Android, and Linux, this device also supports leading browsers. Users can connect through six different form factors, utilizing USB-A, USB-C, NFC, and Lightning interfaces for versatile connectivity.
Related: Will the Futue of Multi-Factor Authentication be annoying?
Summary
You don’t have to keep your fingers crossed, but again I wouldn’t hold my breath. They will be released soon-ish, mainly because FIPS 140-2 certifications will officially conclude on September 21, 2026. After this date, all active certificates will be listed as historical. While FIPS 140-2 modules can still be utilized in existing systems, they cannot be used for new systems. Organizations are encouraged to transition to FIPS 140-3 before this deadline.
@YubiKey, @Yubico, #FIPS, #HSM
Recommend | Xybercraft ™