Enhancing Your System's Kernel Security with Network-Based STIG Techniques
Secure your Ubuntu Linux system by configuring parameters to manage incoming and outgoing packets. This guide simplifies the use of STIG and Enterprise configurations for everyday users.
How to secure Ubuntu’s Kernel to comply with DISA STIG network requirements?
In order to completely do that, it would take more than the following script, but this is a robust set of parameters I highly advise using—in fact, it would take over 500+ tweaks to fully harden your image alone. This isn't even mentioning steps like installing applications such as AIDE or adjusting other settings like enabling/disabling certain firewall rules. I probably should have posted this on my GitHub account, but I may just upload a script there to go with this so it's easier for other users to enable these settings. This is a novice-level procedure, but even if you are new to the Linux family, you can't mess anything up.
Recommend | Xybercraft ™
The kernel-based nature of these settings ensures they are applied at a low level, providing system-wide protection and control over network and system behavior to protect privacy.
Configuring these settings typically involves changes to the /etc/sysctl.conf file.
Using the sysctl command to apply changes is pretty straight forward; Security Technical Implementation Guide (STIG) is:
Based on Department of Defense (DoD) policy and security controls. Implementation guide geared to a specific product and version. Contains all requirements that have been flagged as applicable for the product which have been selected on a DoD baseline.
In other words they are settings you enable (if applicable) on your router, computer, or phone, to make it more secure from attackers and eavesdroppers. Because why not?
What is a Linux Kernel?
The kernel is the part of the operating system that runs with higher privileges while user (space) usually means by applications running with low privileges.
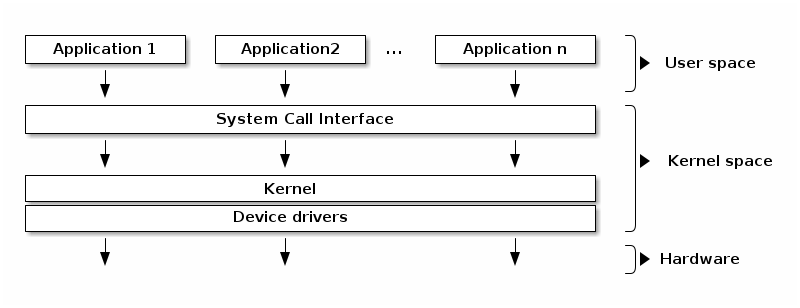
Kernel: The core of the Linux operating system. The kernel is responsible for managing hardware resources, such as CPU, memory, and I/O devices. It provides essential services like process management, memory management, file system management, and network management.
System Libraries: These are the user-space libraries that provide an interface for applications to access kernel services. Examples include the C standard library (glibc), the X Window System libraries, and the graphics libraries (e.g., OpenGL, Vulkan).
Shell and Command-Line Interface (CLI): The shell is the primary user interface for interacting with the operating system. It provides a command-line interface for executing programs, managing files and directories, and automating tasks.
Graphical User Interface (GUI): Many Linux distributions also provide a graphical user interface, such as GNOME, KDE, or Xfce. The GUI allows users to interact with the system using a mouse, windows, icons, and menus.
Applications and Utilities: These are the user-space programs and tools that run on top of the operating system, providing various functionalities, from web browsing to document editing to software development.
The layered architecture of the Linux operating system follows the principle of modularity, where each component is designed to perform a specific set of tasks and interact with the other components through well-defined interfaces.
This modular design allows for greater flexibility, extensibility, and maintainability of the overall system.
Recommend | Xybercraft ™
Setting up your Terminal
Its easy, but if this is your first time experimenting with this type of configurations please use a virtual machine to test and tweak your system, I am not responsible for your mistakes, if you do this correctly you’ll be fine.
Step 1a: Open your terminal and type:
sudo nano /etc/sysctl.confNote: when you are within /etc/sysctl.conf" you will probably see a load of information that isn’t even activated, you can clear the entire section if you want.
Tip: you can copy (including) the # from the list of strings below the (GNU Nano Example) and paste them in your /etc/sysctl.conf to save time, or pick and choose which you want/need.
Step 1b: After you Nano into your Syscrl this is similar to what you will see; except more:
# GNU Nano
#
# /etc/sysctl.conf - Configuration file for setting system variables
# See /etc/sysctl.d/ for additional system variables.
# See sysctl.conf (5) for information.
#
# kernel.domainname = example.com
#
##############################################################
#
# **APPLY RULES HERE AND BELOW**
# **APPLY RULES HERE AND BELOW**
# **APPLY RULES HERE AND BELOW**
#Step 2: Copy and paste or pick and pull.
# Networking Hardening Configuration
# Provided by Xybercraft
# Learn More: https://xyber.substack.com
# IPv4 Settings |
# TCP Hardening
net.ipv4.tcp_challenge_ack = 1
net.ipv4.tcp_sack = 0
net.ipv4.tcp_dsack = 0
net.ipv4.tcp_fack = 0
net.ipv4.tcp_max_orphans = 256
net.ipv4.tcp_mem = # # # (Input Sys., Default Value(s))
# TCP SYN Cookies (IPv4)
net.ipv4.tcp_syncookies = 1
# Disable IP Forwarding
net.ipv4.ip_forward = 0
# Ignore ICMP Broadcast Requests (IPv4)
net.ipv4.icmp_echo_ignore_broadcasts = 1
# Ignore ICMP Redirects (IPv4)
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
# Ignore Secure ICMP Redirects (IPv4)
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
# Disable Sending ICMP Redirects (IPv4)
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
# Ignore Bogus ICMP Error Responses
net.ipv4.icmp_ignore_bogus_error_responses = 1
# Log Martian Packets (IPv4)
net.ipv4.conf.all.log_martians = 1
net.ipv4.conf.default.log_martians = 1
# Networking Hardening Configuration
# Provided by Xybercraft
# Learn More: https://xyber.substack.com
# Disable IPv4 Source Routing
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.conf.default.accept_source_route = 0
# Enable TCP SYN Retries (Mitigate DoS)
net.ipv4.tcp_syn_retries = 5
# Enable TCP SYNACK Retries
net.ipv4.tcp_synack_retries = 2
# Disable TCP Explicit Congestion Notification (ECN)
net.ipv4.tcp_ecn = 0
# Enable Protection Against Time-Wait Assassination Attacks
net.ipv4.tcp_rfc1337 = 1
# Disable TCP Selective Acknowledgments (SACK)
net.ipv4.tcp_sack = 0
# Enable TCP FIN Timeout
net.ipv4.tcp_fin_timeout = 30
# Disable ARP Responses on Unknown Hosts
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
# Enable TCP Keepalive Settings
net.ipv4.tcp_keepalive_time = 600
net.ipv4.tcp_keepalive_intvl = 60
net.ipv4.tcp_keepalive_probes = 5
# Harden TCP Timestamps
net.ipv4.tcp_timestamps = 0
# Networking Hardening Configuration
# Provided by Xybercraft
# Learn More: https://xyber.substack.com
# Disable TCP Window Scaling
net.ipv4.tcp_window_scaling = 0
# Disable Broadcast Packet Responses
net.ipv4.icmp_echo_ignore_broadcasts = 1
# Harden Network Stack Against SYN Flood Attacks
net.ipv4.tcp_max_syn_backlog = 1024
# Reduce the Default TTL Value
net.ipv4.ip_default_ttl = 60
# Disable Proxy ARP
net.ipv4.conf.all.proxy_arp = 0
net.ipv4.conf.default.proxy_arp = 0
# Prevent Fragmentation Attacks
net.ipv4.ipfrag_high_thresh = 262144
net.ipv4.ipfrag_low_thresh = 196608
# Limit the Rate of Incoming ICMP Messages
net.ipv4.icmp_ratelimit = 100
net.ipv4.icmp_ratemask = 88089
# Networking Hardening Configuration
# Provided by Xybercraft
# Learn More: https://xyber.substack.com
# IPv6 Settings |
# Disable IPv6; Note: 1 = Off
net.ipv6.conf.all.disable_ipv6 = 0
net.ipv6.conf.default.disable_ipv6 = 0
net.ipv6.conf.lo.disable_ipv6 = 0
# Disable IP Forwarding (IPv6)
net.ipv6.conf.all.forwarding = 0
# Limit IPv6 Addresses
net.ipv6.conf.all.max_addresses = 2
net.ipv6.conf.default.max_addresses = 2
# Enable IPv6 Privacy Extensions
net.ipv6.conf.all.use_tempaddr = 2
net.ipv6.conf.default.use_tempaddr = 2
# Disable IPv6 Source Routing
net.ipv6.conf.all.accept_source_route = 0
net.ipv6.conf.default.accept_source_route = 0
# Ignore ICMP Redirects (IPv6)
net.ipv6.conf.all.accept_redirects = 0
net.ipv6.conf.default.accept_redirects = 0
# Disable Acceptance of IPv6 Router Advertisements
net.ipv6.conf.all.accept_ra = 0
net.ipv6.conf.default.accept_ra = 0
# Networking Hardening Configuration
# Provided by Xybercraft
# Learn More: https://xyber.substack.com
# Disable IPv6 Duplicate Address Detection
net.ipv6.conf.all.dad_transmits = 1
net.ipv6.conf.default.dad_transmits = 1
# Disable IPv6 Router Solicitations
net.ipv6.conf.all.router_solicitations = 0
net.ipv6.conf.default.router_solicitations = 0
# Disable IPv6 Autoconfig
net.ipv6.conf.all.autoconf = 0
net.ipv6.conf.default.autoconf = 0
# Disable IPv6 Routing Headers
net.ipv6.conf.all.accept_ra_defrtr = 0
net.ipv6.conf.default.accept_ra_defrtr = 0
# Disable IPv6 Router Preference
net.ipv6.conf.all.accept_ra_rtr_pref = 0
# Disable IPv6 Router Lifetime
net.ipv6.conf.all.accept_ra_rt_info_max_plen = 0
net.ipv6.conf.default.accept_ra_rt_info_max_plen = 0
# Disable IPv6 Prefix Information
net.ipv6.conf.all.accept_ra_pinfo = 0
net.ipv6.conf.default.accept_ra_pinfo = 0Step 3a: After you have pasted or configured the script to your desire or network needs, save it with CTRL + X.
Step 3b: You will be prompted “Save modified buffer?” select Yes with Y.
Step 3c: After you press Y it will change to: “File Name to Write: /etc/sysctl.conf”, just press Enter and your screen will clear.
Step 4: Run the following:
sudo sysctl -w net.ipv4.route.flush=1sudo sysctl -w net.ipv6.route.flush=1Step 5: Now to set it.
sudo sysctl -p /etc/sysctl.confYou will see a return output with everything applied that works with your computer, server, router, switch, etc. You can't mess anything up, but you may see odd returns. It means certain strings were set incorrectly. They are easy to fix. I have a few common issues below just in case; if not, reach out in the comment section, and I can help you fix any troubles you encounter.
Step 6: Recommend | Xybercraft ™
Need help? How to fix or Diagnose Issues with /etc/sysctl.conf?
Are you experiencing one of the following? Here are a few common outputs. usually within: Unsupported Parameter, Invalid Value, Module Not Loaded, I have three common ones below bin bold and bulleted.
Problematic Line? Notice the (145)? The error occurs because the line at line 145 in
/etc/sysctl.confis not a validsysctlconfiguration.
sysctl: /etc/sysctl.conf(145): invalid syntax, continuing...Run either:
sed -n '145p' /etc/sysctl.conftail -n +145 /etc/sysctl.conf | head -n 1Which will pull the line (145) to edit or remove the string. is a plain comment or description but is not properly prefixed with a # to mark it as a comment. The sysctl tool tries to interpret it as a configuration directive, which causes the invalid syntax error, meaning you accidentally delete a #, after you find it and replace it. Apply the sysctl settings:
sudo sysctl -p /etc/sysctl.confSetting Key? Which is an Invalid argument and indicates that the value you are trying to set for the (net.ipv4.ipfrag_high_thresh) inst compatible.
sysctl: setting key "net.ipv4.ipfrag_high_thresh": Invalid argumentThe error parameter is not valid for your system or kernel version, which is a simple fix. Lets dig into the cause with:
sysctl -a | grep net.ipv4.ipfrag_high_threshIf the parameter is not listed, it means your kernel does not support it and you will need to sudo nano /etc/sysctl.conf to remove the line causing the issue; or it may be that the required module is not loaded. If the parameter is listed, proceed to verify its current value:
cat /proc/sys/net/ipv4/ipfrag_high_threshYou will get a return number if the parameter exists, ensure that the value you are trying to set is within the valid range. If you set an invalid value (e.g., negative or extremely large), the kernel will reject it. To set a valid value, try:
sudo sysctl -w net.ipv4.ipfrag_high_thresh=YOURRETURNEDVAULEThat should fix your issue. Apply the sysctl settings:
sudo sysctl -p /etc/sysctl.confIf you need this parameter but it is not supported in your current kernel version, consider upgrading to a newer kernel.
Kernel Module(s)
sysctl: cannot stat /proc/sys/net/bridge/bridge-nf-call-ip6tables: No such file or directoryThe error messages you're seeing are caused by the bridge module not being loaded when sysctl tries to apply network bridge settings. To resolve this issue:
sudo modprobe br_netfilterMake sure this doesn’t conflict with your Firewall settings, if it doesn’t go ahead and apply the sysctl settings:
sudo sysctl -p /etc/sysctl.confIf you are experiencing any other issues send me a comment I can help you fix anything wrong. If not you can always reach out to users on Ubuntu’s Stack Exchange, Ubuntu’s Reddit or Ubuntu’s Official Forum.
Summary
I have many setting tweaks to share, and many align with standards that exceed regular requirements to keep you safe and secure, speed up your network/system or help you beef up your battery life.
#STIG #Networking #Security @Ubuntu #Linux
Recommend | Xybercraft ™